| Previous | Next |
1. Solaris TCPIP Protocol Suite (Overview)
2. Planning an IPv4 Addressing Scheme (Tasks
3. Planning an IPv6 Addressing Scheme (Overview)
4. Planning an IPv6 Network (Tasks)
5. Configuring TCP/IP Network Services and IPv4 Addressing (Tasks)
6. Administering Network Interfaces (Tasks)
7. Enabling IPv6 on a Network (Tasks)
8. Administering a TCP/IP Network (Tasks)
9. Troubleshooting Network Problems (Tasks)
10. TCP/IP and IPv4 in Depth (Reference)
12. About Solaris DHCP (Overview)
13. Planning for DHCP Service (Tasks)
14. Configuring the DHCP Service (Tasks)
15. Administering DHCP (Tasks)
16. Configuring and Administering DHCP Clients
17. Troubleshooting DHCP (Reference)
18. DHCP Commands and Files (Reference)
19. IP Security Architecture (Overview)
Protecting Traffic With IPsec (Task Map)
How to Secure Traffic Between Two Systems With IPsec
How to Secure a Web Server With IPsec
How to Generate Random Numbers on a Solaris System
How to Manually Create IPsec Security Associations
How to Verify That Packets Are Protected With IPsec
How to Create a Role for Configuring Network Security
Protecting a VPN With IPsec (Task Map)
How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv4
How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv6
How to Protect a VPN With an IPsec Tunnel in Transport Mode Over IPv4
How to Protect a VPN With an IPsec Tunnel in Transport Mode Over IPv6
21. IP Security Architecture (Reference)
22. Internet Key Exchange (Overview)
24. Internet Key Exchange (Reference)
25. Solaris IP Filter (Overview)
28. Administering Mobile IP (Tasks)
29. Mobile IP Files and Commands (Reference)
30. Introducing IPMP (Overview)
31. Administering IPMP (Tasks)
Part VI IP Quality of Service (IPQoS)
32. Introducing IPQoS (Overview)
33. Planning for an IPQoS-Enabled Network (Tasks)
34. Creating the IPQoS Configuration File (Tasks)
35. Starting and Maintaining IPQoS (Tasks)
36. Using Flow Accounting and Statistics Gathering (Tasks)
Protecting a VPN With IPsec
IPsec tunnels can protect a VPN. In Solaris Express, Developer Edition 2/07, a tunnel can be in tunnel mode, or in transport mode. Tunnel mode is interoperable with the implementation of IPsec by other vendors. Transport mode is interoperable with earlier versions of the Solaris OS. For a discussion of tunnel modes, see Transport and Tunnel Modes in IPsec.
Tunnels in tunnel mode offer more fine-grained control of the traffic. In tunnel mode, for an inner IP address, you can specify the particular protection you want down to a single port. For possible IPsec policies, see the examples that follow the tunnel diagram in Figure 20-1.
Figure 20-1 IPsec Tunnel Diagram
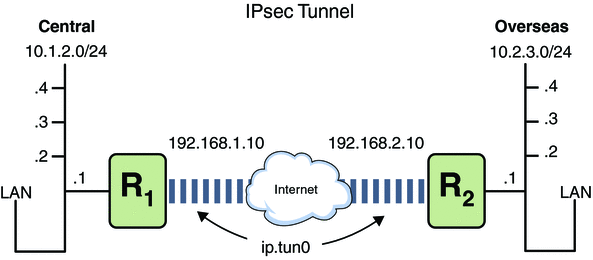
The following examples assume that the tunnel is configured for all subnets of the LANs:
## Tunnel configuration ## ifconfig ip.tun0 10.1.2.1 10.2.3.1 tsrc 192.168.1.10 tdst 192.168.2.10Example 20-3 Creating a Tunnel That All Subnets Can Use
In this example, all traffic from the local LANs in Central in Figure 20-1, can be tunneled through Router 1 to Router 2, and then delivered to all local LANs of Overseas. The traffic is encrypted with AES.
## IPsec policy ##
{tunnel ip.tun0 negotiate tunnel}
ipsec {encr_algs aes encr_auth_algs md5 sa shared}Example 20-4 Creating a Tunnel That Connects Two Subnets OnlyIn this example, only traffic between subnet 10.1.2.0/24 of Central and subnet 10.2.3.0/24 of Overseas is tunneled and encrypted. In the absence of other IPsec policies for Central, if Central attempts to route any traffic for other LANs over this tunnel, the traffic is dropped at Router 1.
## IPsec policy ##
{tunnel ip.tun0 negotiate tunnel laddr 10.1.2.0/24 raddr 10.2.3.0/24}
ipsec {encr_algs aes encr_auth_algs md5 sa shared}Example 20-5 Creating a Tunnel for Only Email Traffic Between Two SubnetsIn this example, a tunnel is created for email traffic only. The traffic is delivered from 10.1.2.0/24 of Central to the email server on the 10.2.3.0/24 subnet of the Overseas LAN. The email is encrypted with Blowfish. The policies apply to the remote and local email ports. The rport policy protects mail that Central sends to the remote email port of Overseas. The lport policy protects mail Central receives from Overseas on local port 25.
## IPsec policy for email from Central to Overseas ##
{tunnel ip.tun0 negotiate tunnel ulp tcp rport 25
laddr 10.1.2.0/24 raddr 10.2.3.0/24}
ipsec {encr_algs blowfish encr_auth_algs md5 sa shared}## IPsec policy for email from Overseas to Central ##
{tunnel ip.tun0 negotiate tunnel ulp tcp lport 25
laddr 10.1.2.0/24 raddr 10.2.3.0/24}
ipsec {encr_algs blowfish encr_auth_algs md5 sa shared}Example 20-6 Creating a Tunnel for FTP Traffic for All SubnetsIn this example, IPsec policy protects the FTP ports in Figure 20-1 with 3DES for all subnets of Central to all subnets of Overseas. This configuration works for the active mode of FTP.
## IPsec policy for outbound FTP from Central to Overseas ##
{tunnel ip.tun0 negotiate tunnel ulp tcp rport 21}
ipsec {encr_algs 3des encr_auth_algs md5 sa shared}
{tunnel ip.tun0 negotiate tunnel ulp tcp lport 20}
ipsec {encr_algs 3des encr_auth_algs md5 sa shared}## IPsec policy for inbound FTP from Central to Overseas ##
{tunnel ip.tun0 negotiate tunnel ulp tcp lport 21}
ipsec {encr_algs 3des encr_auth_algs md5 sa shared}
{tunnel ip.tun0 negotiate tunnel ulp tcp rport 20}
ipsec {encr_algs 3des encr_auth_algs md5 sa shared}The IPv4 procedures in this section assume the following setup. For a depiction of the network, see Figure 20-2.
Each system is using an IPv4 address space.
For a similar example with IPv6 addresses, see How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv6.
Each system has two interfaces. The hme0 interface connects to the Internet. In this example, Internet IP addresses begin with 192.168. The hme1 interface connects to the company's local area network (LAN), its intranet. In this example, intranet IP addresses begin with the number 10.
Each system invokes AH protection with the MD5 algorithm. The MD5 algorithm requires a 128-bit key.
Each system invokes ESP protection with the 3DES algorithm. The 3DES algorithm requires a 192-bit key.
Each system can connect to a router that has direct access to the Internet.
Each system uses shared security associations.
For a description of VPNs, see Virtual Private Networks and IPsec. Figure 20-2 describes the VPN that this procedure configures.
Figure 20-2 Sample VPN Between Offices Separated by the Internet
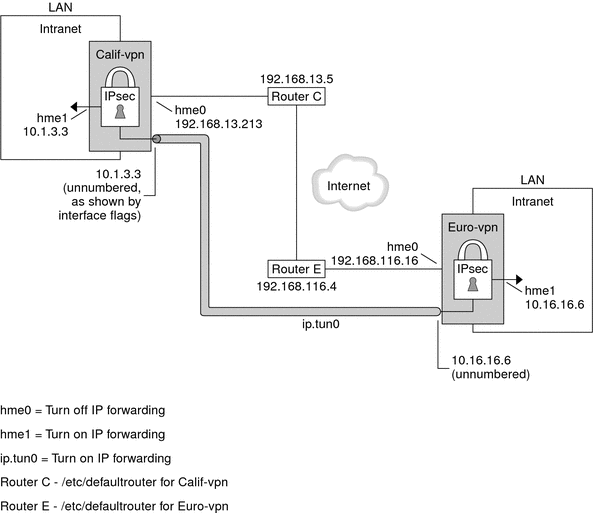
This procedure uses the following configuration parameters.
Parameter |
Europe |
California |
|---|---|---|
System name |
enigma |
partym |
System intranet interface |
hme1 |
hme1 |
System Internet interface |
hme0 |
hme0 |
System intranet address, also the -point address in Step 5 |
10.16.16.6 |
10.1.3.3 |
System Internet address, also the tsrc address in Step 5 |
192.168.116.16 |
192.168.13.213 |
Name of Internet router |
router-E |
router-C |
Address of Internet router |
192.168.116.4 |
192.168.13.5 |
Tunnel name |
ip.tun0 |
ip.tun0 |
How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv4
This procedure extends the procedure, How to Secure Traffic Between Two Systems With IPsec. In addition to connecting two systems, you are connecting two intranets that connect to these two systems. The systems in this procedure function as gateways.
Note - You configure IPsec policy in the global zone.
- On the system console on one of the systems, assume the Primary Administrator
role or become superuser.
The Primary Administrator role includes the Primary Administrator profile. To create the role and assign the role to a user, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
Note - Logging in remotely exposes security-critical traffic to eavesdropping. Even if you somehow protect the remote login, the security of the system is reduced to the security of the remote login session.
- Control the flow of packets before configuring IPsec.
- Ensure that IP forwarding and IP dynamic routing are disabled.
# routeadm Configuration Current Current Option Configuration System State -------------------------------------------------- IPv4 forwarding disabled disabled IPv4 routing default (enabled) enabled …If forwarding and routing are enabled, you can disable them by typing:
# routeadm -d ipv4-routing -d ipv4-forwarding # routeadm -u
Turning off IP forwarding prevents packets from being forwarded from one network to another network through this system. For a description of the routeadm command, see the routeadm(1M) man page.
- Turn on IP strict destination multihoming.
# ndd -set /dev/ip ip_strict_dst_multihoming 1
Turning on IP strict destination multihoming ensures that packets for one of the system's destination addresses arrive at the correct destination address.
When you turn off IP forwarding and turn on IP strict destination multihoming, fewer packets flow all the way through the system. When strict destination multihoming is enabled, packets that arrive on a particular interface must be addressed to one of the local IP addresses of that interface. All other packets, even ones that are addressed to other local addresses of the system, are dropped.
- Disable most network services, and possibly all network services.
Note - If your system was installed with the “limited” SMF profile, then you can skip this step. Network services, with the exception of Solaris Secure Shell, are disabled.
The disabling of network services prevents IP packets from doing any harm to the system. For example, an SNMP daemon, a telnet connection, or an rlogin connection could be exploited.
You have two options.
Run the “limited” SMF profile.
# netservices limited
Or, individually disable network services.
# svcadm disable network/ftp:default # svcadm disable network/finger:default # svcadm disable network/login:rlogin # svcadm disable network/nfs/server:default # svcadm disable network/rpc/rstat:default # svcadm disable network/smtp:sendmail # svcadm disable network/telnet:default # svcs | grep network online Aug_02 svc:/network/loopback:default … online Aug_09 svc:/network/ssh:default …
- Ensure that IP forwarding and IP dynamic routing are disabled.
- On each system, add a pair of SAs between the two systems.
Choose one of the following options:
Configure IKE to manage the keys for the SAs. Use one of the procedures in Configuring IKE (Task Map) to configure IKE for the VPN.
If you have an overriding reason to manually manage the keys, see How to Manually Create IPsec Security Associations.
- On each system, add IPsec policy.
Edit the /etc/inet/ipsecinit.conf file to add the IPsec policy for the VPN. To strengthen the policy, see Example 20-7. For additional examples, see Example 20-3 and following.
- For example, on the enigma system, type the following entry into the ipsecinit.conf
file:
# LAN traffic to and from this host can bypass IPsec. {laddr 10.1.3.3 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {tunnel ip.tun0 negotiate tunnel} ipsec {encr_algs 3des encr_auth_algs md5 sa shared} - On the partym system, type the following entry into the ipsecinit.conf file:
# LAN traffic to and from this host can bypass IPsec. {laddr 10.1.3.3 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {tunnel ip.tun0 negotiate tunnel} ipsec {encr_algs 3des encr_auth_algs md5 sa shared}
- For example, on the enigma system, type the following entry into the ipsecinit.conf
file:
- On each system, configure the tunnel, ip.tun0.
Use the following ifconfig commands to create the point-to-point interface:
# ifconfig ip.tun0 plumb # ifconfig ip.tun0 system1-point system2-point \ tsrc system1-taddr tdst system2-taddr
- For example, on the enigma system, type the following commands:
# ifconfig ip.tun0 plumb # ifconfig ip.tun0 10.16.16.6 10.1.3.3 \ tsrc 192.168.116.16 tdst 192.168.13.213
- On the partym system, type the following commands:
# ifconfig ip.tun0 plumb # ifconfig ip.tun0 10.1.3.3 10.16.16.6 \ tsrc 192.168.13.213 tdst 192.168.116.16
- For example, on the enigma system, type the following commands:
- Protect the tunnel with the IPsec policy that you created.
# ipsecconf
- Bring up the router for the tunnel.
# ifconfig ip.tun0 router up
- On each system, turn on IP forwarding for the hme1 interface.
# ifconfig hme1 router
IP forwarding means that packets that arrive from somewhere else can be forwarded. IP forwarding also means that packets that leave this interface might have originated somewhere else. To successfully forward a packet, both the receiving interface and the transmitting interface must have IP forwarding turned on.
Because the hme1 interface is inside the intranet, IP forwarding must be turned on for hme1. Because ip.tun0 connects the two systems through the Internet, IP forwarding must be turned on for ip.tun0.
The hme0 interface has its IP forwarding turned off to prevent an outside adversary from injecting packets into the protected intranet. The outside refers to the Internet.
- On each system, ensure that routing protocols do not advertise the default route
within the intranet.
# ifconfig hme0 private
Even if hme0 has IP forwarding turned off, a routing protocol implementation might still advertise the interface. For example, the in.routed protocol might still advertise that hme0 is available to forward packets to its peers inside the intranet. By setting the interface's private flag, these advertisements are prevented.
- Manually, add a default route over hme0.
The default route should be a router with direct access to the Internet.
# route add default router-on-hme0-subnet
- For example, on the enigma system, add the following route:
# route add default 192.168.116.4
- On the partym system, add the following route:
# route add default 192.168.13.5
Even though the hme0 interface is not part of the intranet, hme0 does need to reach across the Internet to its peer system. To find its peer, hme0 needs information about Internet routing. The VPN system appears to be a host, rather than a router, to the rest of the Internet. Therefore, you can use a default router or run the router discovery protocol to find a peer system. For more information, see the route(1M) and in.routed(1M) man pages.
- For example, on the enigma system, add the following route:
- Ensure that the VPN starts after a reboot by adding an entry to
the /etc/hostname.ip.tun0 file.
system1-point system2-point tsrc system1-taddr tdst system2-taddr router up
- For example, on the enigma system, add the following entry to the hostname.ip.tun0
file:
10.16.16.6 10.1.3.3 tsrc 192.168.116.16 tdst 192.168.13.213 router up
- On the partym system, add the following entry to the hostname.ip.tun0 file:
10.1.3.3 10.16.16.6 tsrc 192.168.13.213 tdst 192.168.116.16 router up
- For example, on the enigma system, add the following entry to the hostname.ip.tun0
file:
- On each system, configure the interface files to pass the correct parameters to
the routing daemon.
- On the enigma system, modify the /etc/hostname.interface files.
# cat enigma hostname.hme0 10.16.16.6 private
# cat enigma hostname.hme1 192.168.116.16 router
- On the partym system, modify the /etc/hostname.interface files.
# cat partym hostname.hme0 10.1.3.3 private
# cat partym hostname.hme1 192.168.13.213 router
- On the enigma system, modify the /etc/hostname.interface files.
- On each system, run a routing protocol.
You might need to configure the routing protocol before enabling routing. For more information, see Routing Protocols in the Solaris OS. For a procedure, see How to Configure an IPv4 Router.
# routeadm -e ipv4-routing # routeadm -u
In this example, the administrator comments out the bypass policy that was configured in Step 4, thereby strengthening the protection. With this policy configuration, each system on the LAN must activate IPsec to communicate with the router.
# LAN traffic must implement IPsec.
# {laddr 10.1.3.3 dir both} bypass {}
# WAN traffic uses ESP with 3DES and MD5.
{tunnel ip.tun0 negotiate tunnel} ipsec {encr_algs 3des encr_auth_algs md5}Example 20-8 Using IPsec to Protect Telnet Traffic Differently From SMTP TrafficThe first rule protects telnet traffic on port 23 with Blowfish and Sha-1. The second rule protects SMTP traffic on port 25 with AES and MD5.
{laddr 10.1.3.3 ulp tcp dport 23 dir both}
ipsec {encr_algs blowfish encr_auth_algs sha1 sa unique}
{laddr 10.1.3.3 ulp tcp dport 25 dir both}
ipsec {encr_algs aes encr_auth_algs md5 sa unique}Example 20-9 Using an IPsec Tunnel in Tunnel Mode to Protect a Subnet Differently From Other Network TrafficThe following tunnel configuration protects all traffic from subnet 10.1.3.0/24 across the tunnel.
{tunnel ip.tun0 negotiate tunnel laddr 10.1.3.0/24}
ipsec {encr_algs aes encr_auth_algs md5 sa shared}The following tunnel configurations protect traffic from subnet 10.1.3.0/24 to different subnets across the tunnel. Subnets that begin with 10.2.x.x are across the tunnel.
{tunnel ip.tun0 negotiate tunnel laddr 10.1.3.0/24 raddr 10.2.1.0/24}
ipsec {encr_algs blowfish encr_auth_algs md5 sa shared}{tunnel ip.tun0 negotiate tunnel laddr 10.1.3.0/24 raddr 10.2.2.0/24}
ipsec {encr_algs blowfish encr_auth_algs sha1 sa shared}{tunnel ip.tun0 negotiate tunnel laddr 10.1.3.0/24 raddr 10.2.3.0/24}
ipsec {encr_algs aes encr_auth_algs sha1 sa shared}
How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv6
To set up a VPN on an IPv6 network, you follow the same steps as for an IPv4 network. However, the syntax of the commands is slightly different. For a fuller description of the reasons for running particular commands, see How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv4.
This procedure uses the following configuration parameters.
Parameter |
Europe |
California |
|---|---|---|
System name |
enigma |
partym |
System intranet interface |
hme1 |
hme1 |
System Internet interface |
hme0 |
hme0 |
System intranet address |
6000:6666::aaaa:1116 |
6000:3333::eeee:1113 |
System Internet address |
2001::aaaa:6666:6666 |
2001::eeee:3333:3333 |
Name of Internet router |
router-E |
router-C |
Address of Internet router |
2001::aaaa:0:4 |
2001::eeee:0:1 |
Tunnel name |
ip6.tun0 |
ip6.tun0 |
- On the system console on one of the systems, assume the Primary Administrator
role or become superuser.
The Primary Administrator role includes the Primary Administrator profile. To create the role and assign the role to a user, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
Note - Logging in remotely exposes security-critical traffic to eavesdropping. Even if you somehow protect the remote login, the security of the system is reduced to the security of the remote login session.
- Control the flow of packets before configuring IPsec.
For the effects of these commands, see Step 2 in How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv4.
- Ensure that IP forwarding and IP dynamic routing are disabled.
# routeadm Configuration Current Current Option Configuration System State -------------------------------------------------- … IPv6 forwarding disabled disabled IPv6 routing disabled disabledIf forwarding and routing are enabled, you can disable them by typing:
# routeadm -d ipv6-forwarding -d ipv6-routing # routeadm -u
- Turn on IP strict destination multihoming.
# ndd -set /dev/ip ip6_strict_dst_multihoming 1
- Disable most network services, and possibly all network services.
Note - If your system was installed with the “limited” SMF profile, then you can skip this step. Network services, with the exception of Solaris Secure Shell, are disabled.
The disabling of network services prevents IP packets from doing any harm to the system. For example, an SNMP daemon, a telnet connection, or an rlogin connection could be exploited.
You have two options.
Run the “limited” SMF profile.
# netservices limited
Or, individually disable network services.
# svcadm disable network/ftp:default # svcadm disable network/finger:default # svcadm disable network/login:rlogin # svcadm disable network/nfs/server:default # svcadm disable network/rpc/rstat:default # svcadm disable network/smtp:sendmail # svcadm disable network/telnet:default # svcs | grep network online Aug_02 svc:/network/loopback:default … online Aug_09 svc:/network/ssh:default …
- Ensure that IP forwarding and IP dynamic routing are disabled.
- On each system, add a pair of SAs between the two systems.
Choose one of the following options.
Configure IKE to manage the keys for the SAs. Use one of the procedures in Configuring IKE (Task Map) to configure IKE for the VPN.
If you have an overriding reason to manually manage the keys, see How to Manually Create IPsec Security Associations.
- On each system, add IPsec policy.
Edit the /etc/inet/ipsecinit.conf file to add the IPsec policy for the VPN.
- For example, on the enigma system, type the following entry into the ipsecinit.conf
file:
# IPv6 Neighbor Discovery messages bypass IPsec. {ulp ipv6-icmp type 133-137 dir both} pass {} # LAN traffic to and from this host can bypass IPsec. {laddr 6000:6666::aaaa:1116 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {tunnel ip6.tun0 negotiate tunnel} ipsec {encr_algs 3des encr_auth_algs md5 sa shared} - On the partym system, type the following entry into the ipsecinit.conf file:
# IPv6 Neighbor Discovery messages bypass IPsec. {ulp ipv6-icmp type 133-137 dir both} pass {} # LAN traffic to and from this host can bypass IPsec. {laddr 6000:3333::eeee:1113 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {tunnel ip6.tun0 negotiate tunnel} ipsec {encr_algs 3des encr_auth_algs md5 sa shared}
- For example, on the enigma system, type the following entry into the ipsecinit.conf
file:
- On each system, configure a secure tunnel, ip6.tun0.
- For example, on the enigma system, type the following commands:
# ifconfig ip6.tun0 inet6 plumb # ifconfig ip6.tun0 inet6 6000:6666::aaaa:1116 6000:3333::eeee:1113 \ tsrc 2001::aaaa:6666:6666 tdst 2001::eeee:3333:3333
- On the partym system, type the following commands:
# ifconfig ip6.tun0 inet6 plumb # ifconfig ip6.tun0 inet6 6000:3333::eeee:1113 6000:6666::aaaa:1116 \ tsrc 2001::eeee:3333:3333 tdst 2001::aaaa:6666:6666
- For example, on the enigma system, type the following commands:
- Protect the tunnel with the IPsec policy that you created.
# ipsecconf
- Bring up the router for the tunnel.
# ifconfig ip6.tun0 router up
- On each system, turn on IP forwarding for the hme1 interface.
# ifconfig hme1 router
- On each system, ensure that routing protocols do not advertise the default route
within the intranet.
# ifconfig hme0 private
- Manually, add a default route over hme0.
- Ensure that the VPN starts after a reboot by adding an entry
to the /etc/hostname6.ip6.tun0 file.
The entry replicates the parameters that were passed to the ifconfig command in Step 5.
- For example, on the enigma system, add the following entry to the hostname6.ip6.tun0
file:
6000:6666::aaaa:1116 6000:3333::eeee:1113 \ tsrc 2001::aaaa:6666:6666 tdst 2001::eeee:3333:3333 router up
- On the partym system, add the following entry to the hostname6.ip6.tun0 file:
6000:3333::eeee:1113 6000:6666::aaaa:1116 \ tsrc 2001::eeee:3333:3333 tdst 2001::aaaa:6666:6666 router up
- For example, on the enigma system, add the following entry to the hostname6.ip6.tun0
file:
- On each system, configure the interface files to pass the correct parameters to
the routing daemon.
- On the enigma system, modify the /etc/hostname6.interface files.
# cat enigma hostname6.hme0 6000:6666::aaaa:1116 inet6 private
# cat enigma hostname6.hme1 2001::aaaa:6666:6666 inet6 router
- On the partym system, modify the /etc/hostname6.interface files.
# cat partym hostname6.hme0 6000:3333::eeee:1113 inet6 private
# cat partym hostname6.hme1 2001::eeee:3333:3333 inet6 router
- On the enigma system, modify the /etc/hostname6.interface files.
- On each system, run a routing protocol.
# routeadm -e ipv6-routing # routeadm -u
How to Protect a VPN With an IPsec Tunnel in Transport Mode Over IPv4
This procedure extends the procedure, How to Secure Traffic Between Two Systems With IPsec. In addition to connecting two systems, you are connecting two intranets that connect to these two systems. The systems in this procedure function as gateways.
This procedure assumes the same setup as in How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv6.
- On the system console on one of the systems, assume the Primary Administrator
role or become superuser.
The Primary Administrator role includes the Primary Administrator profile. To create the role and assign the role to a user, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
Note - Logging in remotely exposes security-critical traffic to eavesdropping. Even if you somehow protect the remote login, the security of the system is reduced to the security of the remote login session.
- Control the flow of packets before configuring IPsec.
- Ensure that IP forwarding and IP dynamic routing are disabled.
# routeadm Configuration Current Current Option Configuration System State -------------------------------------------------- IPv4 forwarding disabled disabled IPv4 routing default (enabled) enabled …If forwarding and routing are enabled, you can disable them by typing:
# routeadm -d ipv4-routing -d ipv4-forwarding # routeadm -u
Turning off IP forwarding prevents packets from being forwarded from one network to another network through this system. For a description of the routeadm command, see the routeadm(1M) man page.
- Turn on IP strict destination multihoming.
# ndd -set /dev/ip ip_strict_dst_multihoming 1
Turning on IP strict destination multihoming ensures that packets for one of the system's destination addresses arrive at the correct destination address.
When you turn off IP forwarding and turn on IP strict destination multihoming, fewer packets flow all the way through the system. When strict destination multihoming is enabled, packets that arrive on a particular interface must be addressed to one of the local IP addresses of that interface. All other packets, even ones that are addressed to other local addresses of the system, are dropped.
- Disable most network services, and possibly all network services.
Note - If your system was installed with the “limited” SMF profile, then you can skip this step. Network services, with the exception of Solaris Secure Shell, are disabled.
The disabling of network services prevents IP packets from doing any harm to the system. For example, an SNMP daemon, a telnet connection, or an rlogin connection could be exploited.
You have two options.
Run the “limited” SMF profile.
# netservices limited
Or, individually disable network services.
# svcadm disable network/ftp:default # svcadm disable network/finger:default # svcadm disable network/login:rlogin # svcadm disable network/nfs/server:default # svcadm disable network/rpc/rstat:default # svcadm disable network/smtp:sendmail # svcadm disable network/telnet:default # svcs | grep network online Aug_02 svc:/network/loopback:default … online Aug_09 svc:/network/ssh:default …
- Ensure that IP forwarding and IP dynamic routing are disabled.
- On each system, add a pair of SAs between the two systems.
Choose one of the following options:
Configure IKE to manage the keys for the SAs. Use one of the procedures in Configuring IKE (Task Map) to configure IKE for the VPN.
If you have an overriding reason to manually manage the keys, see How to Manually Create IPsec Security Associations.
- On each system, add IPsec policy.
Edit the /etc/inet/ipsecinit.conf file to add the IPsec policy for the VPN. To strengthen the policy, see Example 20-10.
- For example, on the enigma system, type the following entry into the ipsecinit.conf
file:
# LAN traffic to and from this host can bypass IPsec. {laddr 10.1.3.3 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {tunnel ip.tun0 negotiate transport} ipsec {encr_algs 3des encr_auth_algs md5 sa shared} - On the partym system, type the following entry into the ipsecinit.conf file:
# LAN traffic to and from this host can bypass IPsec. {laddr 10.1.3.3 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {tunnel ip.tun0 negotiate transport} ipsec {encr_algs 3des encr_auth_algs md5 sa shared}
- For example, on the enigma system, type the following entry into the ipsecinit.conf
file:
- On each system, configure the tunnel, ip.tun0.
Use the following ifconfig commands to create the point-to-point interface:
# ifconfig ip.tun0 plumb # ifconfig ip.tun0 system1-point system2-point \ tsrc system1-taddr tdst system2-taddr
- For example, on the enigma system, type the following commands:
# ifconfig ip.tun0 plumb # ifconfig ip.tun0 10.16.16.6 10.1.3.3 \ tsrc 192.168.116.16 tdst 192.168.13.213
- On the partym system, type the following commands:
# ifconfig ip.tun0 plumb # ifconfig ip.tun0 10.1.3.3 10.16.16.6 \ tsrc 192.168.13.213 tdst 192.168.116.16
- For example, on the enigma system, type the following commands:
- Protect the tunnel with the IPsec policy that you created.
# ipsecconf
- Bring up the router for the tunnel.
# ifconfig ip.tun0 router up
- On each system, turn on IP forwarding for the hme1 interface.
# ifconfig hme1 router
IP forwarding means that packets that arrive from somewhere else can be forwarded. IP forwarding also means that packets that leave this interface might have originated somewhere else. To successfully forward a packet, both the receiving interface and the transmitting interface must have IP forwarding turned on.
Because the hme1 interface is inside the intranet, IP forwarding must be turned on for hme1. Because ip.tun0 connects the two systems through the Internet, IP forwarding must be turned on for ip.tun0.
The hme0 interface has its IP forwarding turned off to prevent an outside adversary from injecting packets into the protected intranet. The outside refers to the Internet.
- On each system, ensure that routing protocols do not advertise the default route
within the intranet.
# ifconfig hme0 private
Even if hme0 has IP forwarding turned off, a routing protocol implementation might still advertise the interface. For example, the in.routed protocol might still advertise that hme0 is available to forward packets to its peers inside the intranet. By setting the interface's private flag, these advertisements are prevented.
- Manually, add a default route over hme0.
The default route should be a router with direct access to the Internet.
# route add default router-on-hme0-subnet
- For example, on the enigma system, add the following route:
# route add default 192.168.116.4
- On the partym system, add the following route:
# route add default 192.168.13.5
Even though the hme0 interface is not part of the intranet, hme0 does need to reach across the Internet to its peer system. To find its peer, hme0 needs information about Internet routing. The VPN system appears to be a host, rather than a router, to the rest of the Internet. Therefore, you can use a default router or run the router discovery protocol to find a peer system. For more information, see the route(1M) and in.routed(1M) man pages.
- For example, on the enigma system, add the following route:
- Ensure that the VPN starts after a reboot by adding an entry to
the /etc/hostname.ip.tun0 file.
system1-point system2-point tsrc system1-taddr \ tdst system2-taddr encr_algs 3des encr_auth_algs md5 router up
- For example, on the enigma system, add the following entry to the hostname.ip.tun0
file:
10.16.16.6 10.1.3.3 tsrc 192.168.116.16 \ tdst 192.168.13.213 router up
- On the partym system, add the following entry to the hostname.ip.tun0 file:
10.1.3.3 10.16.16.6 tsrc 192.168.13.213 \ tdst 192.168.116.16 router up
- For example, on the enigma system, add the following entry to the hostname.ip.tun0
file:
- On each system, configure the interface files to pass the correct parameters to
the routing daemon.
- On the enigma system, modify the /etc/hostname.interface files.
# cat enigma hostname.hme0 10.16.16.6 private
# cat enigma hostname.hme1 192.168.116.16 router
- On the partym system, modify the /etc/hostname.interface files.
# cat partym hostname.hme0 10.1.3.3 private
# cat partym hostname.hme1 192.168.13.213 router
- On the enigma system, modify the /etc/hostname.interface files.
- On each system, run a routing protocol.
You might need to configure the routing protocol before enabling routing. For more information, see Routing Protocols in the Solaris OS. For a procedure, see How to Configure an IPv4 Router.
# routeadm -e ipv4-routing # routeadm -u
In this example, the administrator comments out the bypass policy that was configured in Step 4, thereby strengthening the protection. With this policy configuration, each system on the LAN must activate IPsec to communicate with the router.
# LAN traffic must implement IPsec.
# {laddr 10.1.3.3 dir both} bypass {}
# WAN traffic uses ESP with 3DES and MD5.
{tunnel ip.tun0 negotiate transport} ipsec {encr_algs 3des encr_auth_algs md5}Example 20-11 Using Deprecated Syntax to Configure an IPsec Tunnel in Transport ModeIn this example, administrator is connecting a Solaris Express system with a system that is running the Solaris 10 release. Therefore, the administrator uses Solaris 10 syntax in the configuration file, and includes the IPsec algorithms in the ifconfig command.
In Step 4, the syntax is the following:
# LAN traffic to and from this address can bypass IPsec. {laddr 10.1.3.3 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {} ipsec {encr_algs 3des encr_auth_algs md5}For Step 5 to Step 7, the syntax is the following:
# ifconfig ip.tun0 plumb # ifconfig ip.tun0 10.16.16.6 10.1.3.3 \ tsrc 192.168.116.16 tdst 192.168.13.213 \ encr_algs 3des encr_auth_algs md5 # ifconfig ip.tun0 router up
# ifconfig ip.tun0 plumb # ifconfig ip.tun0 10.16.16.6 10.1.3.3 \ tsrc 192.168.116.16 tdst 192.168.13.213 \ encr_algs 3des encr_auth_algs md5
The IPsec policy that is passed to the ifconfig commands must be the same as the IPsec policy in the ipsecinit.conf file. Upon reboot, each system reads the ipsecinit.conf file for its policy.
In Step 11, the syntax is the following:
10.16.16.6 10.1.3.3 tsrc 192.168.116.16 \ tdst 192.168.13.213 encr_algs 3des encr_auth_algs md5 router up
How to Protect a VPN With an IPsec Tunnel in Transport Mode Over IPv6
To set up a VPN on an IPv6 network, you follow the same steps as for an IPv4 network. However, the syntax of the commands is slightly different. For a fuller description of the reasons for running particular commands, see How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv4.
This procedure uses the following configuration parameters.
Parameter |
Europe |
California |
|---|---|---|
System name |
enigma |
partym |
System intranet interface |
hme1 |
hme1 |
System Internet interface |
hme0 |
hme0 |
System intranet address |
6000:6666::aaaa:1116 |
6000:3333::eeee:1113 |
System Internet address |
2001::aaaa:6666:6666 |
2001::eeee:3333:3333 |
Name of Internet router |
router-E |
router-C |
Address of Internet router |
2001::aaaa:0:4 |
2001::eeee:0:1 |
Tunnel name |
ip6.tun0 |
ip6.tun0 |
- On the system console on one of the systems, assume the Primary Administrator
role or become superuser.
The Primary Administrator role includes the Primary Administrator profile. To create the role and assign the role to a user, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
Note - Logging in remotely exposes security-critical traffic to eavesdropping. Even if you somehow protect the remote login, the security of the system is reduced to the security of the remote login session.
- Control the flow of packets before configuring IPsec.
For the effects of these commands, see Step 2 in How to Protect a VPN With an IPsec Tunnel in Tunnel Mode Over IPv4.
- Ensure that IP forwarding and IP dynamic routing are disabled.
# routeadm Configuration Current Current Option Configuration System State -------------------------------------------------- … IPv6 forwarding disabled disabled IPv6 routing disabled disabledIf forwarding and routing are enabled, you can disable them by typing:
# routeadm -d ipv6-forwarding -d ipv6-routing # routeadm -u
- Turn on IP strict destination multihoming.
# ndd -set /dev/ip ip6_strict_dst_multihoming 1
- Disable most network services, and possibly all network services.
Note - If your system was installed with the “limited” SMF profile, then you can skip this step. Network services, with the exception of Solaris Secure Shell, are disabled.
The disabling of network services prevents IP packets from doing any harm to the system. For example, an SNMP daemon, a telnet connection, or an rlogin connection could be exploited.
You have two options.
Run the “limited” SMF profile.
# netservices limited
Or, individually disable network services.
# svcadm disable network/ftp:default # svcadm disable network/finger:default # svcadm disable network/login:rlogin # svcadm disable network/nfs/server:default # svcadm disable network/rpc/rstat:default # svcadm disable network/smtp:sendmail # svcadm disable network/telnet:default # svcs | grep network online Aug_02 svc:/network/loopback:default … online Aug_09 svc:/network/ssh:default …
- Ensure that IP forwarding and IP dynamic routing are disabled.
- On each system, add a pair of SAs between the two systems.
Choose one of the following options.
Configure IKE to manage the keys for the SAs. Use one of the procedures in Configuring IKE (Task Map) to configure IKE for the VPN.
If you have an overriding reason to manually manage the keys, see How to Manually Create IPsec Security Associations.
- On each system, add IPsec policy.
Edit the /etc/inet/ipsecinit.conf file to add the IPsec policy for the VPN.
- For example, on the enigma system, type the following entry into the ipsecinit.conf
file:
# IPv6 Neighbor Discovery messages bypass IPsec. {ulp ipv6-icmp type 133-137 dir both} pass {} # LAN traffic can bypass IPsec. {laddr 6000:6666::aaaa:1116 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {tunnel ip6.tun0 negotiate transport} ipsec {encr_algs 3des encr_auth_algs md5} - On the partym system, type the following entry into the ipsecinit.conf file:
# IPv6 Neighbor Discovery messages bypass IPsec. {ulp ipv6-icmp type 133-137 dir both} pass {} # LAN traffic can bypass IPsec. {laddr 6000:3333::eeee:1113 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {tunnel ip6.tun0 negotiate transport} ipsec {encr_algs 3des encr_auth_algs md5}
- For example, on the enigma system, type the following entry into the ipsecinit.conf
file:
- On each system, configure a secure tunnel, ip6.tun0.
- For example, on the enigma system, type the following commands:
# ifconfig ip6.tun0 inet6 plumb # ifconfig ip6.tun0 inet6 6000:6666::aaaa:1116 6000:3333::eeee:1113 \ tsrc 2001::aaaa:6666:6666 tdst 2001::eeee:3333:3333
- On the partym system, type the following commands:
# ifconfig ip6.tun0 inet6 plumb # ifconfig ip6.tun0 inet6 6000:3333::eeee:1113 6000:6666::aaaa:1116 \ tsrc 2001::eeee:3333:3333 tdst 2001::aaaa:6666:6666
- For example, on the enigma system, type the following commands:
- On each system, turn on IP forwarding for the hme1 interface.
# ifconfig hme1 router
- On each system, ensure that routing protocols do not advertise the default route
within the intranet.
# ifconfig hme0 private
- Manually, add a default route over hme0.
- Ensure that the VPN starts after a reboot by adding an entry to
the /etc/hostname6.ip6.tun0 file.
The entry replicates the parameters that were passed to the ifconfig command in Step 5.
- For example, on the enigma system, add the following entry to the hostname6.ip6.tun0
file:
6000:6666::aaaa:1116 6000:3333::eeee:1113 \ tsrc 2001::aaaa:6666:6666 tdst 2001::eeee:3333:3333 router up
- On the partym system, add the following entry to the hostname6.ip6.tun0 file:
6000:3333::eeee:1113 6000:6666::aaaa:1116 \ tsrc 2001::eeee:3333:3333 tdst 2001::aaaa:6666:6666 router up
- For example, on the enigma system, add the following entry to the hostname6.ip6.tun0
file:
- On each system, configure the interface files to pass the correct parameters to
the routing daemon.
- On the enigma system, modify the /etc/hostname6.interface files.
# cat enigma hostname6.hme0 6000:6666::aaaa:1116 inet6 private
# cat enigma hostname6.hme1 2001::aaaa:6666:6666 inet6 router
- On the partym system, modify the /etc/hostname6.interface files.
# cat partym hostname6.hme0 6000:3333::eeee:1113 inet6 private
# cat partym hostname6.hme1 2001::eeee:3333:3333 inet6 router
- On the enigma system, modify the /etc/hostname6.interface files.
- On each system, run a routing protocol.
# routeadm -e ipv6-routing # routeadm -u
In this example, administrator is connecting a Solaris Express system with a system that is running the Solaris 10 release. Therefore, the administrator uses Solaris 10 syntax in the configuration file, and includes the IPsec algorithms in the ifconfig command. The steps are performed in the same order, but uses the Solaris 10 syntax.
In Step 4, the syntax is the following:
# IPv6 Neighbor Discovery messages bypass IPsec. {ulp ipv6-icmp type 133-137 dir both} pass {} # LAN traffic can bypass IPsec. {laddr 6000:3333::eeee:1113 dir both} bypass {} # WAN traffic uses ESP with 3DES and MD5. {} ipsec {encr_algs 3des encr_auth_algs md5}For Step 5 to Step 7, the syntax is the following:
# ifconfig ip6.tun0 inet6 plumb # ifconfig ip6.tun0 inet6 6000:6666::aaaa:1116 6000:3333::eeee:1113 \ tsrc 2001::aaaa:6666:6666 tdst 2001::eeee:3333:3333 \ encr_algs 3des encr_auth_algs md5 # ifconfig ip6.tun0 inet6 router up
The IPsec policy that is passed to the ifconfig commands must be the same as the IPsec policy in the ipsecinit.conf file. Upon reboot, each system reads the ipsecinit.conf file for its policy.
In Step 9, the syntax is the following:
6000:6666::aaaa:1116 6000:3333::eeee:1113 \ tsrc 2001::aaaa:6666:6666 tdst 2001::eeee:3333:3333 \ encr_algs 3des encr_auth_algs md5 router up
| Previous | Next |